 Recon
Recon
The fastest, most effective way to rigorously red team your AI apps.

Scalable Red Teaming for AI
Deploy Your AI Confidently
Recon provides your team the insights to make data-informed decisions about potential risks before you launch AI apps to production. Along with vulnerability assessments, Recon also gives actionable insights for model selection and evaluation of your AI defenses.
Accelerate AI Testing
Recon systematically tests and retests AI apps in a few hours, across multiple threat vectors with an attack library of 450+ known attacks on AI systems, an AI Agent scan, and the ability to bring your own custom library. You can leverage Recon on its own or use it to supercharge your existing red team.
Stay Ahead of Attackers
Recon leverages a community of over 17,000 security researchers, as well as first-party and academic research, to identify and prepare for new threat vectors. With weekly updates to our attack library, threat research is always driving the product, so you know that you are building securely no matter what the latest model or threat is.
Key Features
Extensive Attack Library
Recon’s extensive Attack Library spans six major threat categories and is continuously updated to counter zero-day and emerging attack techniques. Using trained LLMs as detectors, Recon delivers accuracy, not just coverage, to ensure your systems remain protected against a wide range of evolving vulnerabilities with limited false positives.

Precise, Relevant Red Team Attacks
Recon tests the AI app, not just the model. Recon’s Agent creates relevant attacks that leverage a range of inputs, from the business objective of the application to the base model, deployed guardrails, RAG pipelines, and relevant system prompts.
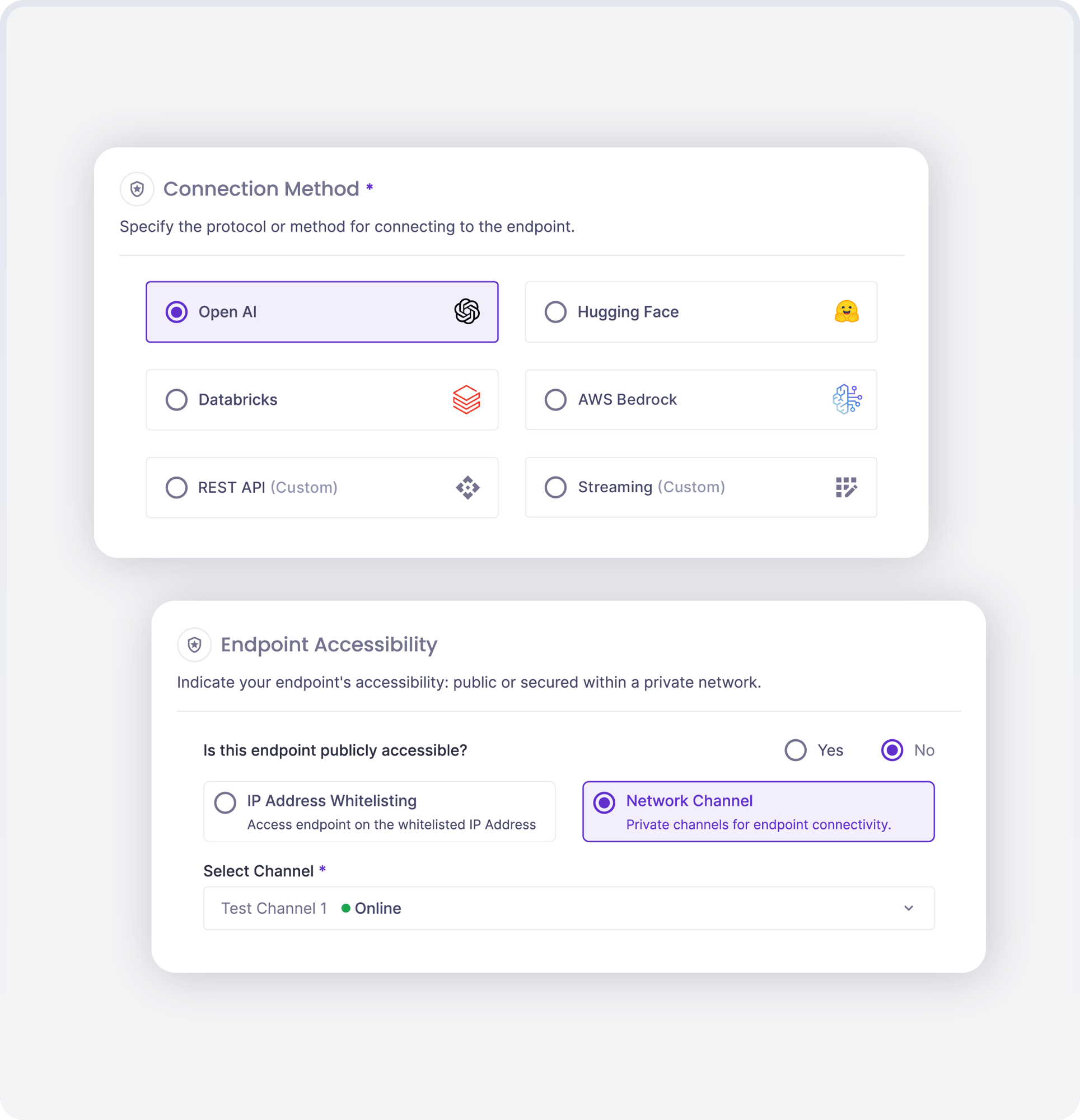
Augmented Red Teaming
Red teamers can work collaboratively with Recon, using Natural Language to set attack goals—no code necessary. Recon produces in-depth, conversation-level visibility to support risk analysis and remediation.

Bring-Your-Own Attack Prompts
Enhance your security evaluations with the ability to run custom attack prompt sets. Users can upload bespoke prompts to simulate specific threat scenarios, powered by our proprietary detection algorithms that precisely reflect your environment’s unique needs.

Reporting and Framework Mapping
Recon easily exports results to CSV and JSON to enable quick and effective collaboration across teams. Vulnerabilities are also mapped to standard frameworks such as OWASP Top 10 for LLMs, DASF, and more, making it fast and easy to meet compliance standards.

Explore the Latest from Protect AI
Are You Ready to Start Securing Your AI End-to-End?
Request a demo to see firsthand what makes Recon the fastest, most effective way to rigorously red team your AI apps.




